- Security overview
- Privacy and GDPR
- What data does Situm store?
- How does Situm anonymize de device identifiers?
- Where do we store the data?
- Who else will have access to the data?
- What provisions has Situm put in place to ensure GDPR compliance?
- Can I use Situm Services if I have customers in the UE?
- Can I use Situm Services if my customers are outside the UE?
- Where can I learn more about this topic?
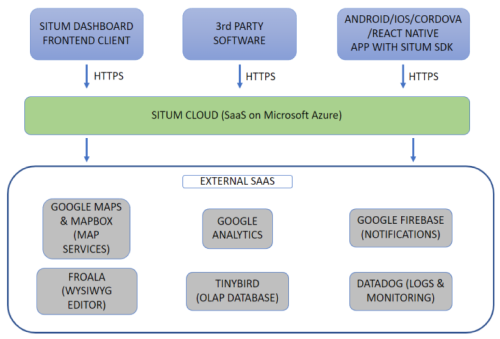
Situm is provided as a Software as a Service, hosted in the Microsoft Azure cloud. As shown in the diagram below, Situm may receive secure communications (HTTPS) from:
- Situm Web Dashboard.
- Apps that integrate Situm mobile SDKs (Android / iOS / Cordova).
- 3rd party software (via REST APIs).
Situm platform receives and computes those requests using Microsoft Azure cloud platform (West Europe region). Situm data (cartography, geolocations…) is also mostly stored in Microsoft Azure cloud (see our Master Subscription Agreement for more details).
On the other hand, Situm makes use of some 3rd party software itself. The most important services are:
- Google Maps. Base maps provider used by Situm Web Dashboard.
- Mapbox. More base maps provider used by Situm Web Dashboard.
- Froala. Rich Text plugin, used for entering Rich Text in POIs, geofences, etc.
- Google Analytics. For the aggregated analysis of the use of Situm Dashboard.
- Google Firebase. Crashlytics (register app events for debugging purposes), Remote Config (notify users when new app versions are available), Google Analytics for Firebase (aggregated analysis of the use of apps), and notifications in general.
- Tinybird. OLAP databased for fast analytics.
- Datadog. Logs & monitoring.
Security overview #
At Situm, we want to offer the maximum guarantees of compliance with security and data protection requirements. Security is an integral part of our products, processes and services that we are continuously reviewing to maintain the highest standards of compliance.
Security as a fundamental pillar #
Data security is a fundamental pillar when developing our products, processes and services. We approach the design of all functionalities and changes in our architecture with a mindset of:
- Compliance with GDPR guidelines.
- Privacy by design and by default.
- Data gobernance accountability.
- Continuous improvement.
That is why security at Situm is integrated into the day-to-day life of all workers and all improvements to our software, processes and services are always made with security in mind. Our cloud is designed to respond to a multitude of challenges in different industries with different security requirements. In order to meet them, we aim at meeting the highest standards across all industries.
Reliability #
Situm Platform is a central part of many business applications and end-customer oriented applications. We understand the importance of reliability in our platform and hence we have put in place a series of measures to ensure it.
SLA #
We aim to provide at least 99.9% of uptime and solve critical requests in a few hours at most. Please read our SLA in Exhibit B of our MSA for more details: https://situm.es/assets/docs/situm-masteragreement.pdf
Availability and Redundancy #
Situm Platform provides high-availability and redundancy by default. Situm services replicas run on multiple nodes with the ability to scale vertically and horizontally.
In addition, to ensure maximum availability, we host our platform and data on Microsoft Azure. Microsoft Azure data centers are designed to provide high availability for the applications they host, and Situm follows Azure’s best practices in order to make the most of the capabilities provided by Azure.
Avoiding data losses: redundant storage and backups #
Situm secures all the data in multiple ways to avoid losses.
- Redundant storage. All the data is stored in redundant systems by default.
- Incremental daily backup. Automatic incremental backups of all the data are generated daily.
- Complete weekly copy. In addition to incremental daily backups, a full weekly backup is generated to maximize recoverability.
Backups are encrypted with RSA 4096 asymmetric keys. Backups are kept for 45 days (in case of database information) or 60 days (in case of files, such as images).
Business continuity and disaster recovery #
Ensuring the continuity of our service (and your business) is a key priority at Situm. These are the main elements that help us in minimizing the impact of any eventuality:
- Continuous logging and monitoring. Situm Platform logs the interactions with its APIs and monitors the network traffic for early trouble detection (with automatic internal alerts).
- Redundant backup storage. Backups are replicated in different Azure geographical regions within Europe in order to avoid a full data/service loss in the (very unlikely) event that a whole Microsoft Azure data center or geographical area fails.
- Restoration & integrity tests. We perform daily, weekly, and quarterly tests (with different level of granularity and detail) to ensure that the restoration procedures work as expected and that the backup data is recoverable.
Product Security #
Password and API key protection with role-based data segmentation #
Situm Platform is protected from unwanted data access through password and/or APIKEY based authentication & authorization.
- Passwords must meet a minimum complexity (8 characters with at least one digit, one lowercase, one uppercase, one special character) and, in case the user forgets them, can be re-generated through email validation.
- APIKEYs can be generated in order to consume Situm APIs from 3rd party systems, such as web apps or your Situm-based mobile apps.
Situm users can be segmented into different roles, each role having different data accesses. Similarly, API keys can have different permission levels: positioning-only (allows mobile apps to perform indoor/outdoor positioning), read-only, and read & write.
Encryption and key management #
Data encryption is performed at different levels to ensure a complete protection:
- Encryption in transit. We use “Transport Layer Security (TLS) 1.2 or higher” protocol for all communications that go through public networks such as the Internet.
- Encryption at rest. Microsoft Azure provides “Encryption at rest” in all the storage services that we use. In addition, Azure manages the encryption keys automatically, thus helping to avoid potential key leaks.
Password policy #
Situm Platform users’ passwords need to have a minimum complexity of 8 alphanumeric characters. We store these passwords properly hashed and encrypted, so it is not possible to recover them. Nevertheless, passwords can be regenerated by email at user request (automatically, without our intervention).
Client isolation #
Different users/clients share the same physical infrastructure, but Situm provides logical isolation between the data of different users/clients. This isolation ensures that actions performed by a certain client will not compromise the data of other clients.
Vulnerability / incident management #
Situm has established an internal incident and vulnerability management policy following the GDPR guidelines. This includes, among other measures, early evaluation of any data breach and communication to affected customers (or to the data protection agency) depending on the severity of the incidents.
Data operations #
Data processed & stored #
Please read our GDPR section for a description and list of the data that Situm processes and stores.
Accessing the client data for maintenance #
At Situm, only a few employees have access to client data for maintenance, based on an appropriate segmentation of roles and responsibilities within the company. All employees are required to abide by a corporate password policy that includes, among others, measurements such as periodic key renewals.
Access to client data is continuously monitored. Non-authorized accesses are treated as data breaches. Physical access to data centers is protected by Microsoft security policies and measurements.
Accessing the client data for customer support #
Our Customer Success team (customer support) will only access client data if it is strictly necessary to solve a ticket or request raised by the client.
Data destruction #
Situm follows GDPR guidelines for data destruction. More info in our MSA.
Privacy and GDPR #
Situm is GDPR compliant because when you use Situm, you trust us with your data. This is why we have implemented all the security and privacy measures that allow us to protect your data and ensure your rights. We take our obligation to safeguard users’ personal information very seriously and are committed to protecting the privacy and security of our users, while being transparent about our data practices.
What data does Situm store? #
The following information is a summary of the data that Situm could process:
- Mobile device information. This information includes: geolocation, sensor readings (e.g. WiFi readings), device information (e.g. OS), app information (e.g. package name, SDK version), etc. All the device information is associated with an unique pseudo-anonymous identifier of the device (not of the user) that ensures their privacy.
- Device identifier: Situm utilizes anonymized device identifiers to ensure user privacy. For Android devices, the identifier is based on the Android ID, while for iOS devices, it is derived from the Identifier for Vendor (IDFV). These identifiers are not based on the MAC address or any other specific hardware component and are generated by the devices themselves. They are unique and persistent, allowing for the identification of returning devices, as long as the identifiers remain the same. However, certain factors, such as app uninstallation and reinstallation, may cause these identifiers to change.
- Situm Dashboard users information. We also store some information of the users that are registered on the Situm Dashboard (e.g. the administrator account), such as: email address and contact information provided by the user, OS, cookies, etc.
- Cartography information of those buildings that are uploaded to the Situm Dashboard: floorplans, points of interest, etc. This information is not considered as personal data of the user.
- Logging data of user interactions with Situm Services, such as device IP, accessed URL, etc.
- In case the user activates the “Workforce Tracking” module (Situm MRM), other additional information may be processed, such as: historical relationship of devices (and their IDs) to which each user has been associated with, alarms generated by the users, etc.
The most sensitive data that Situm stores is the geolocation data (indoor and/or outdoor) of each device that runs Situm SDK. To ensure maximum privacy protection, Situm does not associate this information with the user by default, but to the anonymized device identifier described above.
For a complete list of the data, see Annex I of Situm Master Subscription Agreement.
How does Situm anonymize de device identifiers? #
Situm is committed to ensuring the privacy and security of its users. One of the ways it achieves this is by utilizing anonymized device identifiers for both Android and iOS platforms. This section explains how these identifiers are generated and anonymized for each platform.
Android Devices #
For Android devices, Situm uses the Android ID as a base to create the anonymized device identifier. The Android ID is a 64-bit random number generated by the Android system when the app is installed on the device. This number, represented as a hexadecimal string, is not based on any specific hardware component or personal information of the user. The Android ID is inherently anonymized by design and does not require any additional techniques to anonymize it.
iOS Devices #
For iOS devices, Situm uses the Identifier for Vendor (IDFV) as a base to create the anonymized device identifier. The IDFV is a Universally Unique Identifier (UUID) generated based on the vendor of the app installed on an iOS device. Similar to the Android ID, the IDFV is not derived from any specific hardware component or personal information of the user. The IDFV is also inherently anonymized by design and does not require any further techniques to anonymize it.
Anonymization Process #
The anonymization of device identifiers in Situm occurs at the device level during their generation. As the Android ID and IDFV are not based on any identifiable information like the MAC address, they are considered anonymized by design. This ensures that the privacy of users is maintained, and no personal information can be traced back to the device or the user through these identifiers.
Device Identifier renewal. #
Both Android and iOS platforms can generate new device identifiers upon app reinstallation. However, the behavior may vary between the two platforms.
On Android, starting with Android Oreo (8.0, API level 26), per-app Android IDs have been introduced. This means that when an app is uninstalled and then reinstalled, the system may generate a new Android ID for that specific app, effectively renewing the device identifier.
On iOS, the Identifier for Vendor (IDFV) can also be renewed through app reinstallation. When all apps from the same vendor are uninstalled and then reinstalled on the device, a new IDFV is generated for the reinstalled apps, which renews the device identifier.
Where do we store the data? #
Situm trusts Microsoft Azure as its cloud provider. Azure has stated that is compliant with the most relevant security and privacy policies, as well as the GDPR provisions.
By default, Situm stores all the data in Europe (West Europe region). We are also aware that you may prefer to store your data in other geographies, and we offer this option too.
Just send us an email to sales@situm.com with your case and we will help you in this regard.
Who else will have access to the data? #
Situm trusts several data subprocessors to ensure the maximum quality of the service, such as Microsoft Azure or Google Maps. Our Annex II of Situm Master Subscription Agreement (MSA) contains a full list of subprocessors.
What provisions has Situm put in place to ensure GDPR compliance? #
We’ve been working hard to ensure that we’re in compliance with the GDPR. The following is a non-exhaustive list of the main provisions:
- Situm has appointed a Data Protection Offices that foresees the GDPR compliance of the organization. You can reach to the Situm DPO by writing an email at dpo@situm.com.
- Situm has adequately put in place a “Data Processing Addendum” that regulates the GDPR provisions for the personal data treatment. It is available for review in our Situm Master Subscription Agreeent (MSA) (Section 8, Exhibit B and Annexes I y II).
- Situm supervises GDPR compliance by performing the recommended GDPR internal procedures, such as the Privacy Impact Assessment, applying UE standard contractual clauses, etc.
- Situm has put in place the security measures and policies required to adequately protect your data, including privacy by design, backup and disaster recovery policy, access control protection, password policy, device inventory policy, data encryption policy, data breach action protocol, security and GDPR staff training, etc.
We will continue to review our security measures, as we always do, to warrant the compliance of the GDPR provisions and the European Data Protection Board recommendations.
Can I use Situm Services if I have customers in the UE? #
Yes! The main purpose of the GDPR is to protect and grants data subjects specific rights to their personal data. Understanding these rights and how to comply with them as a Data Controller is essential to comply with the GDPR provisions. Situm will be acting as a Data Processor for your customer’s data and will provide ways to comply with all of your data subject’s rights under the GDPR obligations of a data processor. As Data Controller, you will need to inform to the UE users which data are you collecting that may be considered personal, including the data that Situm Services process from the users, and determinate how you will use the users consent or other lawful basis when Situm will be processing personal data as your Data Processor. You can check our “Data Processing Agreement” at the Exhibit D of the Situm MSA.
Can I use Situm Services if my customers are outside the UE? #
Of course! We warrant the compliance of the GDPR by default because we are established at UE, which has one of the highest regulations for security of personal data. If your customers are outside the UE, you will also have these high standard security measures required by the GDPR. In any case, you can also contact our team (dpo@situm.com) for more information on your needs of personal data protection.
Where can I learn more about this topic? #
Please check:
- Section 8, Exhibit B and Annexes I y II of Situm Master Subscription Agreement (MSA).
- Our Privacy Policy.
Or write us an email to dpo@situm.com.


